Table of contents
On the web, generally, data are transmitted in plain text between the server to the client leaving it vulnerable to eavesdropping. That’s where SSL comes into the picture.
SSL aka Secure Sockets Layer is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser. SSL allows sensitive information like credit card numbers, social numbers, passports, login credentials securely.
What does it look like?
SSL certificates have a key pair.
- A public key.
- A private key.
These keys work together to establish an encrypted connection. The certificate also contains the “Subject”, which is the identity of the owner.
When a browser attempts to access a website that is secured with an SSL or TLS (successor of SSL), the browser and the web server establish an SSL connection using a process called SSL handshake.
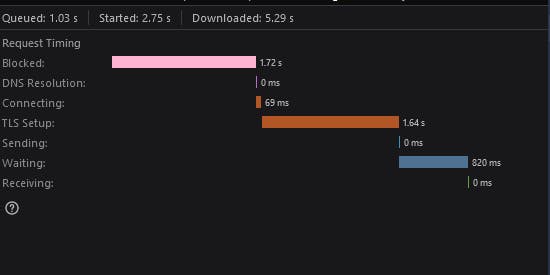
If we deep dive any site network tool we can discover how much time was taken to omit the SSL/TLS handshake process.
Essentially three keys are used to set up the SSL connection.
- Public
- Private
- Session
Anything encrypted with the public key can be decrypted with the private key and vice versa as well. So it's a time-consuming process and it takes some compute power to achieve that but it is only used during the SSL handshake to create a symmetric session key. After the connection is established, the session key is used to do all kinds of encryption and decryption.
How does it work?
There are some steps to create this encrypted channel from the client to the server. let's just say we want to connect to this site pritompurkayasta.me.
- At first browser sends a request to that address so that the server can identify itself with a proper certificate.
- Server sends a copy of its SSL certificate (Public Key)
- Client (Browser) checks the certificate root against a list of trusted CAs and the certificate expiry, unrevoked, and the common name validation for the website that it is connecting to. If the browser trusts the certificate, it will create, encrypt the data using the server's public key and send back the response to the server.
- Then server decrypts the response with the session key using its private key and sends the acknowledgment session key to start the encrypted session between the server and the client.
- Now server and the client transmitted data with this session key for further communication.
Types of certificates?
There are three types of certificates that exist as what I have found on the internet.
- Single Domain Certification. (For a single domain name.)
- Wildcard Certification. (Single Domain certificate + Subdomain validation)
- Multidomain Certification. (Many websites)
There are also some certification validation levels.
- Domain Validation. (For specific domain name, Basic level of SSL)
- Organization Validation. (Additional Checks with the SSL issuer)
- Extended Validation. (Thorough check of the business that’s behind the purchase, Most secure level of SSL)

